When files disappear on a Mac, recovery isn’t always as simple as it sounds. Apple has built macOS around speed, security, and reliability – and while that’s great for everyday use, it complicates things when something goes wrong. The APFS file system handles data in ways that make traditional recovery methods less effective.
FileVault encryption adds another layer of protection, but it can also lock out recovery tools entirely. Then there’s TRIM – a feature that helps SSDs stay quick and efficient by wiping free space, often erasing traces of lost data for good. Together, these technologies make Macs great at protecting data but surprisingly tough when you need to get that data back.
Understanding macOS File Systems and Security
The advanced design of the macOS operating system makes file recovery after deletion more complex. The T2 chip and Apple Silicon processors (M1, M2, and M3) function as storage controllers and encryption processors, which operate directly from the logic board to boost system security.
The system maintains automatic encryption of data, which stays protected when users remove the storage device. The recovery process needs both the original hardware and firmware that match the system configuration to prevent traditional forensic tools from working.
APFS: Reliability at the Cost of Recoverability
How APFS Works?
APFS manages data using metadata containers and copy-on-write (CoW) techniques. Instead of overwriting data blocks directly, it writes new data elsewhere and updates the metadata pointer. This improves consistency, allowing the system to maintain duplicates or “snapshots” without interrupting operations.
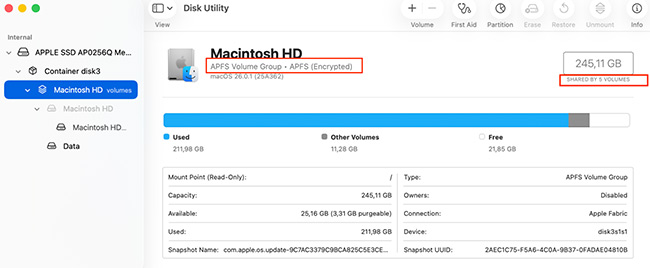
This same efficiency leads to problems for recovery experts. When data is deleted, APFS typically marks the associated blocks as free immediately. Without an easy way to track which blocks hold a particular file, recovery tools find it exceptionally difficult to reconstruct the file system layout.
Common APFS Recovery Issues
The most frequent failures occur when:
- APFS containers become un-mountable due to volume header corruption.
- Snapshots malfunction, preventing access even to backups.
- Logical directory damage renders Disk Utility unable to repair files.
Getting Around APFS Limitations
Speed of action is key. Once block reuse begins, previous data fragments are irretrievably lost. Running deep scans before powering the system repeatedly gives recovery software the best chance of finding intact metadata records. When available, Time Machine remains the most reliable way to restore missing files or entire system images.
Encryption: FileVault and Hardware Security
How FileVault Works
FileVault 2 uses XTS‑AES‑128 encryption with 256‑bit keys to protect entire system volumes, which are stored in the Secure Enclave of T2 chips or Apple Silicon processors. The encryption process makes SSD data inaccessible to unauthorized users because the decryption key exists within the Secure Enclave of the T2 chip or Apple Silicon processor.
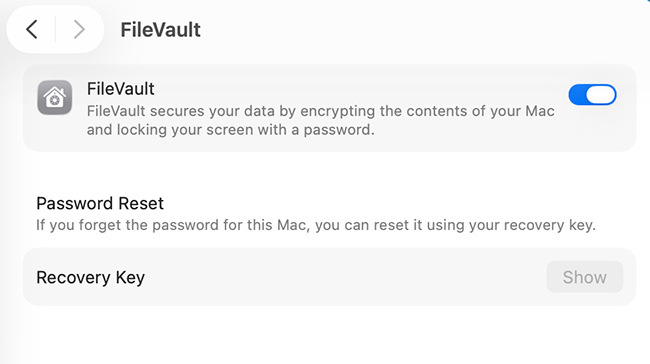
The system design creates a recovery problem because it ties decryption keys to hardware components. The drive shows only encrypted data when users try to access it through external means or replace their logic board. The data becomes permanently unavailable when users fail to provide their password or recovery key.
Real‑World Recovery Barriers
Typical failure points include:
- Hardware damage that destroys the Secure Enclave containing decryption keys.
- Forgotten passwords or missing recovery keys.
- Firmware corruption that prevents the system from authenticating encrypted volumes.
Even professional labs face near‑impossible odds when these conditions align. The keys cannot be cloned or extracted due to Apple’s cryptographic restrictions.
Tips for Encrypted‑Volume Users
- The FileVault recovery key requires storage in an independent location that is not connected to the device.
- Time Machine and cloud storage provide backup solutions for non-sensitive data through unencrypted processes, which should run at scheduled intervals.
- Avoid enabling FileVault on temporary systems unless necessary for compliance.
While encryption safeguards privacy, it also eliminates virtually any route to post‑failure data recovery.
TRIM: The Invisible Data Eraser
The TRIM function operates automatically on Macs with SSD storage because it helps maintain flash memory efficiency. The SSD controller receives TRIM instructions to mark sectors as unnecessary after users delete files. The drive then clears them in the background to optimize performance.
Why TRIM Makes Recovery Nearly Impossible
Unlike spinning hard drives, SSDs don’t leave data remnants after a TRIM operation. Once executed, the physical blocks holding the deleted file are wiped clean, leaving recovery software with zero usable fragments. Modern macOS releases perform TRIM automatically during idle periods and after every reboot – meaning that time is critical.
Best Practices During Deletion Events
If you accidentally delete important data:
- Power down immediately. Avoid letting TRIM finish erasing freed sectors.
- Do not restart or install new software on the affected drive.
- Attempt recovery only through external boot drives or recovery tools running in macOS Recovery Mode.
The recovery of data becomes possible when using older systems or external SSDs that have TRIM disabled, but Apple Silicon Macs prevent users from disabling TRIM.
Hardware-Level Obstacles
Apple’s trend toward soldered solid-state drives – bonded directly to the motherboard – has eliminated removable storage. This means recovery specialists can no longer extract the storage module and image it separately. Any damage to the CPU or power circuitry can thus render the entire drive unreadable.
T2 and Apple Silicon Constraints
In T2 and M-series machines, components like the SSD controller, key manager, and Secure Enclave are integrated into one package. The encryption key exists only within that chip. For recovery, labs need the original motherboard in working condition, including its associated hardware. Without it, neither chip-off methods nor controller swaps can reconstruct the data.
Professional services occasionally perform board-level recoveries by repairing power rails or shorted circuits to bring the device temporarily online. Yet success rates remain much lower than with pre‑2018 Mac models.
Improving Recovery Outcomes: Practical Steps
Act immediately after data loss:
- Shut the system down the moment deletion is discovered.
- Press Command + R for Intel-based Macs or hold the power button for M1, M2-chip Macs to boot into macOS Recovery Mode.
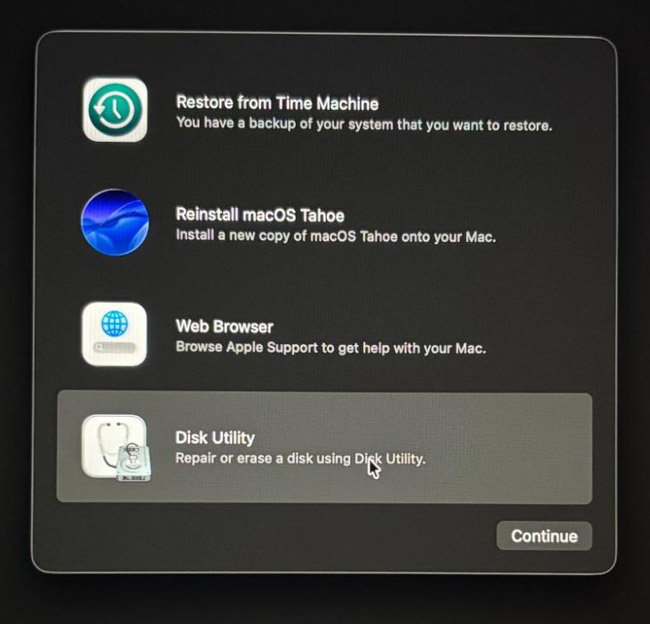
- Go to Disk Utility > First Aid for minor logical issues, but avoid reinstalling macOS.
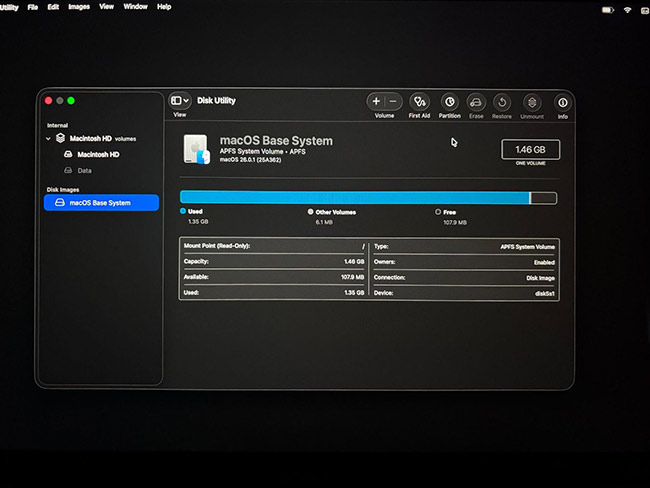
The volume can be recovered through an external recovery tool such as R‑Studio or iBoysoft Data Recovery when accessed from another Mac if the volume fails to mount.
How to Prevent Data Loss and Maintain System Health
The most critical step against permanent loss is maintaining routine backups.
- The Time Machine system needs to run from an external drive, which performs automatic snapshots every hour.
- Go to Settings > General > Time Machine > Add Backup Disk.
- The system requires cloud replication through iCloud Drive or Backblaze to achieve off-site data redundancy.
- Verify your backup integrity monthly by restoring random files. Many users discover too late that their drives weren’t backing up properly due to permission errors or full disks.
Smart Habits for a Healthier Mac
Regular system maintenance helps detect file system anomalies early:
- Run Disk Utility’s First Aid monthly.
- Third-party defragmenters should be avoided because SSDs do not have bugs.
- Business-critical Macs require centralized backup monitoring and deployment to support their operations.
- The operating system should receive regular updates because they fix APFS and firmware-related issues.
Use redundancy. Apple’s ecosystem integrates well with third‑party automation tools – use them to ensure no data point exists in a single copy only.
Conclusion
Apple introduced new file system technologies, encryption methods, and solid-state drive solutions, which have redefined how users achieve a balance between system speed and data protection and data restoration capabilities. APFS’s design minimizes fragmentation but accelerates data erasure.
FileVault’s encryption protects users but locks data behind unbreakable security, and TRIM ensures SSD longevity at the cost of recoverability. In practice, this means that by the time a user realizes their files are lost, recovery often becomes impossible without backups or hardware‑level repairs. The best strategy isn’t to rely on recovery – it’s to plan for failure.


